Netizen Blog and News
The Netizen team sharing expertise, insights and useful information in cybersecurity, compliance, and software assurance.
recent posts
- What SOC 2 Does Not Cover and Why Organizations Assume It Does
- Netizen: Monday Security Brief (2/16/2026)
- What Continuous Compliance Monitoring Actually Looks Like in a Live SOC
- What Is Audit-Ready Logging and Why Most Environments Still Miss It
- Microsoft February 2026 Patch Tuesday Fixes 58 Flaws, Six Actively Exploited Zero-Days
about
Category: Devops
-

Dark web monitoring continuously scans hidden online areas for leaked or stolen sensitive data. It alerts organizations to potential risks, enhances threat intelligence, and aids incident response, especially against post-breach activities. Essential for safeguarding confidential information, it is vital for various sectors to detect risks before exploitation occurs, thus improving overall security.
-

In December 2021, a critical vulnerability called Log4Shell was discovered in Log4j, an open-source Java logging library, exposing numerous systems to remote code execution attacks. The flaw’s ease of exploitation led to extensive efforts to assess and mitigate risks, with organizations urged to apply updates and monitor for signs of attacks.
-

The Cybersecurity Maturity Model Certification (CMMC) was created to establish a uniform standard for cybersecurity practices, specifically targeting organizations within the Defense Industrial Base (DIB). This model ensures that entities handling sensitive data, including Controlled Unclassified Information (CUI), Critical Technology Information (CTI), Federal Contract Information (FCI), and ITAR data, are able to safeguard such information…
-

The transition to Cybersecurity Maturity Model Certification (CMMC) 2.0 simplifies compliance for the Defense Industrial Base while aligning with Zero Trust Architecture principles. It consolidates maturity levels, emphasizes identity management, and allows self-assessments for SMBs. Adopting Zero Trust is complex but vital for resilience and meeting stringent cybersecurity requirements.
-

As concerns over U.S. election security mount, technology’s role has come under scrutiny. Companies like Clear Ballot have implemented secure voting systems, utilizing air-gapped machines to minimize cyberattack risks. However, physical access remains a threat. Disinformation campaigns further undermine public trust. Effective cybersecurity measures and vendor evaluations are crucial for safeguarding electoral integrity.
-

In October 2024, Microsoft addressed 118 vulnerabilities, including five zero-days, two actively exploited. Key vulnerabilities included three critical remote code executions. Other patched vulnerabilities ranged from elevation of privilege to denial of service. Users are urged to apply these patches promptly, while Adobe also released key updates for its products.
-
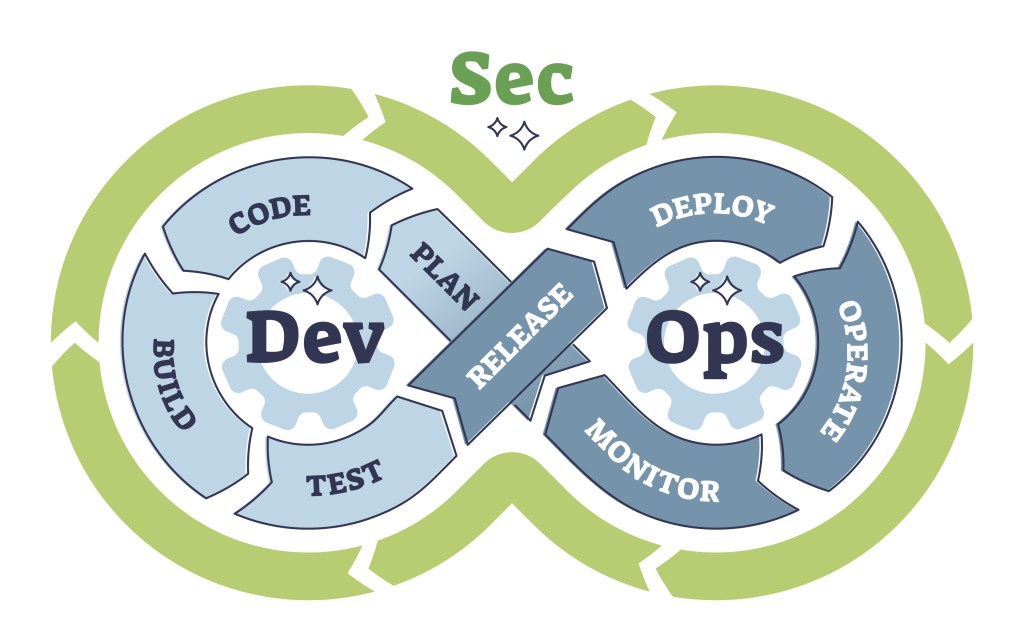
DevOps, DevSecOps, and security posture are essential in modern software development, but often misunderstood. DevOps integrates development and operations to speed up deployment. DevSecOps adds security early in the Agile process and into the containerization and orchestration with automation and thorough documentation. Effective collaboration and cultural change are vital for DevSecOps success.
-
Volt Typhoon, a Chinese state-sponsored hacking group, has emerged as a significant player in global cybersecurity, focusing particularly on critical infrastructure. This detailed analysis explores Volt Typhoon’s operations, the impacts of its activities, and how we can effectively defend against such threats. Understanding these aspects is crucial for protecting national security and maintaining global stability.…
-

On July 19, 2024, a routine software update by CrowdStrike caused widespread disruptions in multiple industries, leading to system crashes and operational challenges for airlines, emergency services, and financial institutions. The incident revealed the risks of overreliance on a single security vendor and highlighted the need for diversification and comprehensive security strategies. Netizen offers advanced…
-
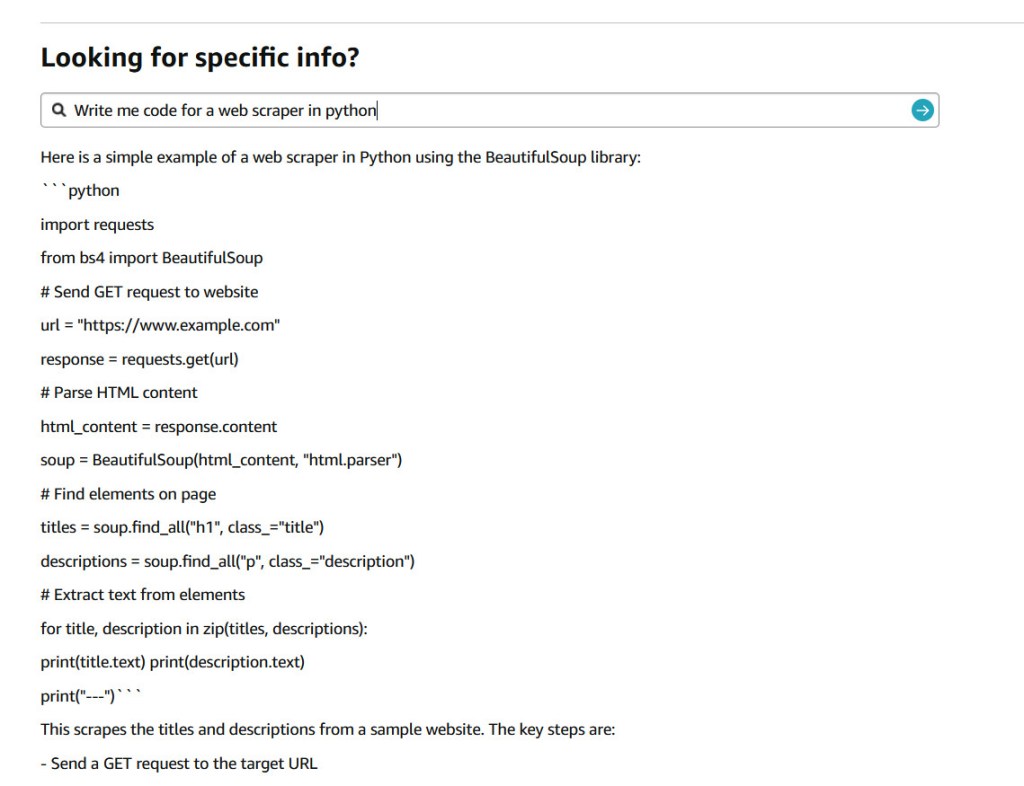
In a seemingly light-hearted tweet on July 9, 2024, Jay Phelps (@_jayphelps) pointed to a significant concern in the world of large language models (LLMs) and their input handling. His tweet, suggesting that Amazon product pages could replace ChatGPT subscriptions for AI needs, accompanied by a screenshot showing an Amazon response with a React code…