Netizen Blog and News
The Netizen team sharing expertise, insights and useful information in cybersecurity, compliance, and software assurance.
recent posts
- Netizen: Monday Security Brief (2/9/2026)
- Why Inherited Controls Make SOC-as-a-Service the Practical Compliance Model
- CVE-2026-25253: One-Click RCE in OpenClaw via Token Leakage and WebSocket Abuse
- Netizen: Monday Security Brief (2/2/2026)
- Human Context Protocol: An Integrity-First Security Architecture for Trustworthy AI Agents
about
Category: Business
-
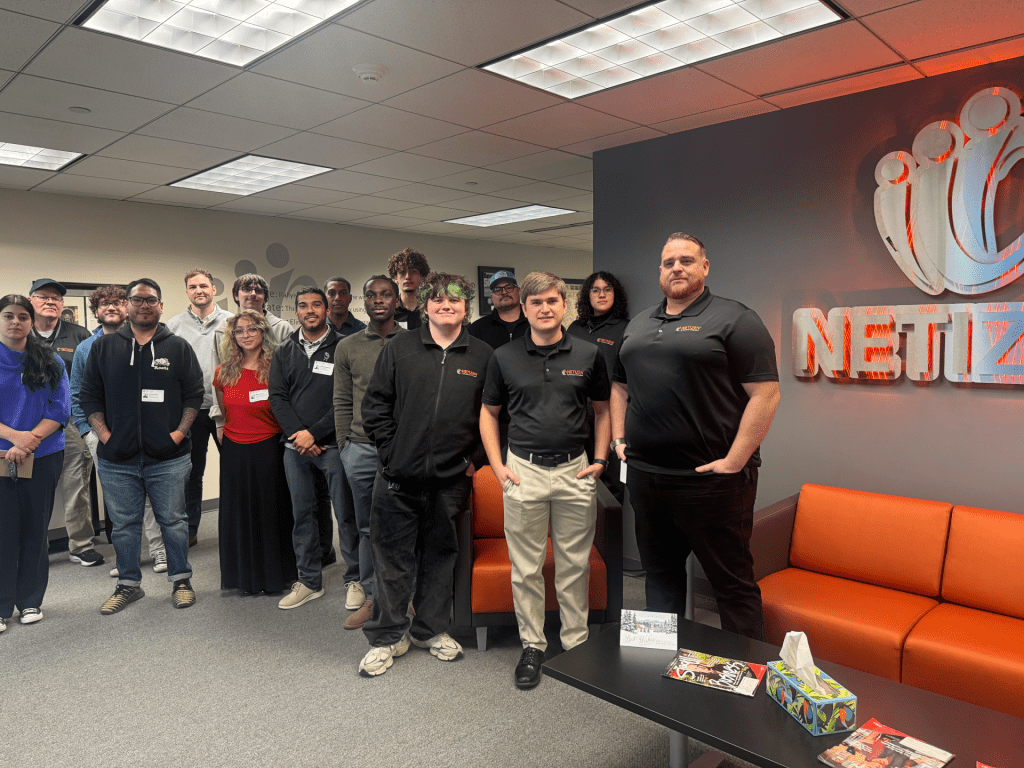
Allentown, PA: Students spent the morning inside Netizen’s 24x7x365 Security Operations Center, observing how analysts monitor systems, investigate alerts, and respond to real security activity as it unfolds. Rather than a simulated exercise, the visit focused on how a production SOC functions day to day, giving students direct exposure to the tools, workflows, and decision-making…
-

Small and mid-sized businesses increasingly depend on automated security tools to defend their environments. Endpoint agents, vulnerability scanners, cloud security dashboards, and automated alerting platforms promise broad coverage with minimal staffing. For organizations under cost pressure, automation feels like a rational tradeoff. The issue is not that these tools lack value; it is that automation…
-

The expiration of the Cybersecurity Information Sharing Act (CISA) disrupts the legal framework for threat intelligence sharing, leading organizations to reevaluate their collaboration strategies. Without CISA’s protections, companies face new privacy and liability challenges, prompting a shift toward privacy engineering, enhanced vendor scrutiny, and a need for stronger governance to maintain effective information exchange.
-

Initial Access Brokers (IABs) facilitate cybercrime by breaking into networks and selling access to other criminals, particularly in the context of Ransomware-as-a-Service (RaaS). As access prices drop and targeting broadens, even small businesses are now at risk. Organizations need robust security measures to detect IAB-driven intrusions early and mitigate threats.
-

The Simple Network Management Protocol (SNMP) is crucial for network monitoring but poses security risks, especially in its earlier versions. Older versions, SNMPv1 and SNMPv2c, transmit credentials in plain text, making them vulnerable to attacks. SNMPv3 offers improved security through authentication and encryption, necessitating careful configuration. Best practices must be followed to mitigate risks effectively.
-

TikTok negotiations continue in the U.S. amid ongoing security concerns, regardless of ownership changes. Experts warn that risks remain due to data collection practices and algorithmic influences. Security teams are advised to treat TikTok as high-risk, implementing restrictions and monitoring to mitigate potential threats to enterprise data and operations.
-

The PCI DSS v4.0 became mandatory on April 1, 2025, replacing version 3.2.1. Key updates include strengthened authentication, enhanced encryption, and automated monitoring. Compliance is essential to avoid penalties and reputational damage. Netizen offers guidance for businesses to align with these requirements and ensure successful audits and customer trust.
-
The transition to Security-as-a-Service addresses inadequacies of traditional security models, offering scalable, automated monitoring and compliance solutions. This approach centralizes threat detection and response, leverages shared expertise, and enhances operational efficiency. Organizations benefit from reduced costs, improved detection times, and the ability to focus on strategic security tasks while maintaining compliance and visibility.
-

Cybersecurity Awareness Month often focuses on posters, phishing tests, and all-hands emails reminding employees to “think before they click.” While these are useful starting points, the real goal is far more technical: to harden the human layer of defense while integrating people into the broader security architecture. A culture of cybersecurity is only meaningful if…
-

CMMC 2.0 mandates that all defense supply chain businesses, including small and mid-sized companies, meet specific cybersecurity requirements to protect sensitive data. Compliance is crucial for retaining contracts and avoiding penalties. Implementing this framework involves addressing various cybersecurity aspects, and early compliance efforts may offer competitive advantages.