Overview:
- Phish Tale of the Week
- React2Shell, One Month Later: What We Now Know
- One of the Largest Insurance Data Breaches of 2025: Aflac Confirms 22.65 Million Impacted
- How can Netizen help?
Phish Tale of the Week
Ofteften times phishing campaigns, created by malicious actors, target users by utilizing social engineering. For example, in this text message, the actors are appearing as an unnamed organization. The message politely explains that they’re about to invest in a stock “projected to deliver a 60 percent return this week.” It seems both urgent and genuine, so why shouldn’t we respond yes? Luckily, there’s plenty of reasons that point to this being a scam.
Here’s how we can tell not to fall for this smish:
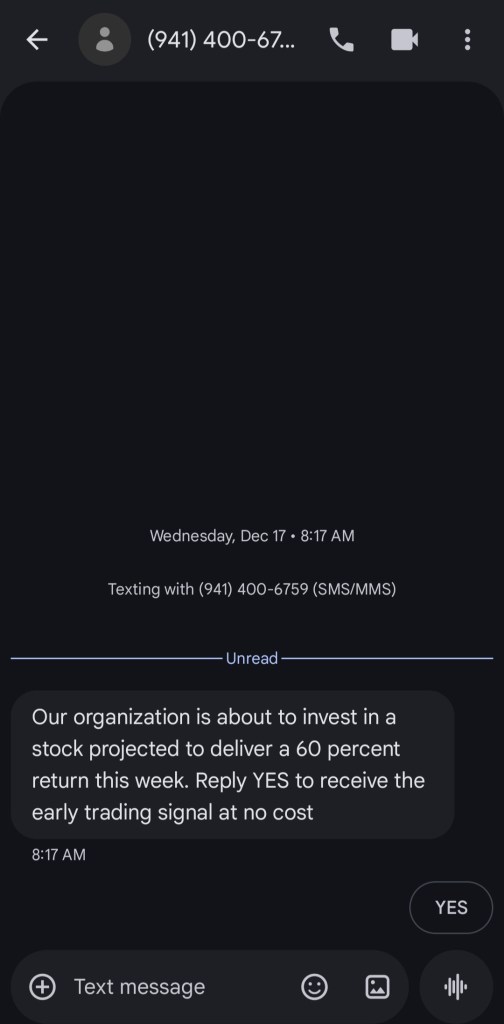
- The first warning sign for this SMS is the fact that we do not recognize the number or the sender. Legitimate financial institutions and service providers clearly identify themselves in their messages and usually contact customers through verified channels. When a text arrives from an unknown number with no context, it should always be treated with caution, especially if it relates to money, investments, or account activity. Unsolicited investment messages are a common red flag, since reputable firms do not cold-text offers like this.
- The second warning sign in this text is the messaging itself. This message tries to push you into acting quickly by promising a “60 percent return” and stating that this will happen “this week.” Smishing and phishing scams often rely on urgency so that recipients react emotionally instead of stopping to verify the source. It is always wise to slow down and review the tone and claims in any text before clicking links or replying.
- The final warning sign for this SMS is the lack of any verifiable sender identity or legitimate business details. Real investment firms identify themselves clearly, include required disclosures, and do not make sweeping claims about guaranteed or near-term profits. This text asks you to reply “YES,” which is a common tactic used by scammers to confirm that your number is active and to draw you further into the scheme. All of these elements point to this being a smishing attempt rather than a genuine investment opportunity.
General Recommendations:
A smishing attack will typically direct the user to click on a link where they will then be prompted to update personal information, such as a password, credit card, social security, or bank account information. A legitimate company already has this sensitive information and would not ask for it again, especially via your text messages.
- Scrutinize your messages before clicking anything. Have you ordered anything recently? Does this order number match the one I already have? Did the message come from a store you don’t usually order supplies from or a service you don’t use? If so, it’s probably a phishing attempt.
- Verify that the sender is actually from the company sending the message.
- Did you receive a message from someone you don’t recognize? Are they asking you to sign into a website to give Personally Identifiable Information (PII) such as credit card numbers, social security number, etc. A legitimate company will never ask for PII via instant message or email.
- Do not give out personal or company information over the internet.
- Do not click on unrecognized links or attachments. If you do proceed, verify that the URL is the correct one for the company/service and it has the proper security in place, such as HTTPS.
Many smishing messages pose a sense of urgency or even aggressiveness to prompt a form of intimidation. Any SMS requesting immediate action should be vetted thoroughly to determine whether or not it is a scam. Also, beware of messages that seek to tempt users into opening an attachment or visiting a link. For example, an attachment titled “Fix your account now” may draw the question “What is wrong with my account?” and prompt you to click a suspicious link.
Cybersecurity Brief
In this month’s Cybersecurity Brief:
React2Shell, One Month Later: What We Now Know

About a month after the disclosure of React2Shell, the unauthenticated remote code execution flaw affecting React Server Components, the conversation has shifted from breaking news to reflection. At first, the headlines focused on urgency, exploitation speed, and the sheer number of affected deployments. With time to review the research and incident reports, the picture has become clearer. The story is less about a single CVE and more about what it revealed about modern application stacks.
React2Shell was impactful because exposure flowed from the framework layer itself. Organizations using default React and Next.js deployments inherited risk even if their custom code was clean. Research teams from Wiz, Unit 42, Google, AWS, and others aligned on the same fundamental point: unsafe handling of serialized component data inside the server-side pipeline created a direct path to remote code execution. No unusual configuration was required. For many environments, simply being on default settings was enough.
The tempo of exploitation quickly became a defining theme. Proof-of-concept exploit code appeared soon after disclosure, followed by automated scanning activity. Some honeypots saw compromise in only a few minutes. Threat intelligence teams confirmed that both state-linked and financially motivated attackers were involved. Reports did not just describe shell access. They documented backdoors, tunneling tools, miners, and botnet implants, which showed that adversaries viewed this as a viable and persistent entry point.
Different security reports complemented one another rather than compete. Wiz and Unit 42 demonstrated consistent exploit reliability across environments. Google and AWS confirmed that exploitation was not theoretical by connecting it to live activity. Huntress documented behavior after access was gained, which helped shift the discussion from exposure to impact. Patrowl contributed nuance by pointing out that some early exposure figures were inflated by noisy scanning patterns. The result was a more mature view of the situation without minimizing the seriousness of the flaw.
A key lesson from the past month relates to long-standing assumptions. For years, many teams treated mainstream frameworks as relatively safe foundations, focusing most defensive energy on custom code, configuration control, and operational discipline. React2Shell challenged that thinking. A widespread framework became a direct access point overnight, and the required response speed exceeded what many patch programs can deliver. Most enterprises cannot upgrade and redeploy critical application infrastructure within hours. Attackers clearly can move inside that window.
Remediation guidance remains straightforward. Patches for React and downstream frameworks such as Next.js are available and should be applied quickly. The second part of the response is deeper. Since exploitation began almost immediately, teams should evaluate whether affected systems were reachable during the exposure window and review them for post-compromise activity, such as unexpected processes, persistence tools, or outbound tunneling traffic. Version checks alone cannot answer that question.
To read more about this article, click here.
One of the Largest Insurance Data Breaches of 2025: Aflac Confirms 22.65 Million Impacted

Aflac has confirmed that personal information belonging to roughly 22.65 million people was stolen during a cyber intrusion first detected in June 2025. The company initially disclosed the incident on June 20 after identifying suspicious activity on its U.S. network on June 12. While the attack did not deploy ransomware or disrupt operations, the scope of exposed data makes this one of the most significant insurance sector breaches of the year.
After completing its investigation in December, Aflac reported that files accessed during the intrusion contained personal data belonging to customers, beneficiaries, employees, agents, and others associated with the company. The compromised information includes names, addresses, Social Security numbers, dates of birth, driver’s license details, government ID numbers, and medical and health insurance information. In some cases, additional sensitive identifiers may also have been included.
Aflac stated that the attack originated from a sophisticated cybercrime group and indicated that the breach appeared to be part of a broader campaign targeting the insurance industry. While the company did not attribute the incident to a specific actor, the timeline aligns with reporting from Google’s Threat Intelligence Group that flagged increased targeting of insurance providers by the group commonly referred to as Scattered Spider.
The company noted that it is not aware of any confirmed misuse of the stolen data at this time. Even so, the sensitivity of the information involved raises clear concerns about identity fraud, medical identity abuse, and long-tail financial risk. To help mitigate potential harm, Aflac is offering affected individuals 24 months of credit monitoring, identity theft protection services, and medical fraud protection support.
Notifications are now underway, and impacted individuals are being urged to monitor financial and medical accounts closely, remain alert to potential phishing or social engineering attempts, and make use of the protection services being offered. The investigation reinforced a broader warning already circulating in the sector: organized threat groups continue to prioritize insurance companies, and the scale of data under management amplifies the consequences when defenses falter.
To read more about this article, click here.
How Can Netizen Help?
Founded in 2013, Netizen is an award-winning technology firm that develops and leverages cutting-edge solutions to create a more secure, integrated, and automated digital environment for government, defense, and commercial clients worldwide. Our innovative solutions transform complex cybersecurity and technology challenges into strategic advantages by delivering mission-critical capabilities that safeguard and optimize clients’ digital infrastructure. One example of this is our popular “CISO-as-a-Service” offering that enables organizations of any size to access executive level cybersecurity expertise at a fraction of the cost of hiring internally.
Netizen also operates a state-of-the-art 24x7x365 Security Operations Center (SOC) that delivers comprehensive cybersecurity monitoring solutions for defense, government, and commercial clients. Our service portfolio includes cybersecurity assessments and advisory, hosted SIEM and EDR/XDR solutions, software assurance, penetration testing, cybersecurity engineering, and compliance audit support. We specialize in serving organizations that operate within some of the world’s most highly sensitive and tightly regulated environments where unwavering security, strict compliance, technical excellence, and operational maturity are non-negotiable requirements. Our proven track record in these domains positions us as the premier trusted partner for organizations where technology reliability and security cannot be compromised.
Netizen holds ISO 27001, ISO 9001, ISO 20000-1, and CMMI Level III SVC registrations demonstrating the maturity of our operations. We are a proud Service-Disabled Veteran-Owned Small Business (SDVOSB) certified by U.S. Small Business Administration (SBA) that has been named multiple times to the Inc. 5000 and Vet 100 lists of the most successful and fastest-growing private companies in the nation. Netizen has also been named a national “Best Workplace” by Inc. Magazine, a multiple awardee of the U.S. Department of Labor HIRE Vets Platinum Medallion for veteran hiring and retention, the Lehigh Valley Business of the Year and Veteran-Owned Business of the Year, and the recipient of dozens of other awards and accolades for innovation, community support, working environment, and growth.
Looking for expert guidance to secure, automate, and streamline your IT infrastructure and operations? Start the conversation today.

Leave a comment